Chapter 5 Digital Security Ethics and Privacy
Mar 7 Current Conditions. Our records are carefully stored and protected thus cannot be accessed by unauthorized persons.

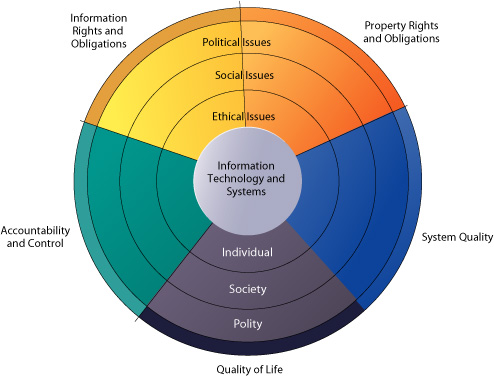
Ethical Security Issues In Information System
It includes physical administrative and technical safeguards.

. National security emergency preparedness nsef part 910. Information Technology for Development. Interviews reviews and much more.
Now is a pivotal time for the workplace and workforce as critical issues affecting society impact work. 22 1968 82 Stat. 1190712h or m and except that the court in a criminal case may order that certain information required by law or agency rule to be given to the person arrested be maintained in a confidential manner and exempt from the provisions of s.
Amazons Big Reviews Row. CBS2 News Chicagos weather forecast model First Alert helps digital users and traditional television viewers stay on top of Chicagos dynamic weather. Get all the latest India news ipo bse business news commodity only on Moneycontrol.
The society also sponsors a Speakers Bureau which invites speakers who are keenly aware of the motivations that drive. Amazon blocked fan reviews until 72 hours after the shows Prime Video debut so that it could better evaluate whether armchair critics actually watched the show. We do not disclose clients information to third parties.
Get 247 customer support help when you place a homework help service order with us. Employee responsibilities and conduct. Cyber security cyber crime cyber ethics social media cloud computing android apps.
The cyber security techniques ethics and the trends changing the face of cyber security. Globalization has accelerated since the 18th century due to advances in transportation and communications technologyThis increase in global interactions has caused a growth in. Editorial Notes Codification.
1078 known as the Federal Reports Act of 1942 which was classified to sections 139 to 139f of former Title 5 transferred to chapter 12 421 et seq of former Title 44 and. Privacy act notification access and amendment procedures. 5 The activities of the JBS include distributing literature pamphlets magazines videos and other material.
A value-focused thinking exploration in understanding users privacy and security concerns. Members of chapters that grew larger than 20 members were expected to break off and form a new small chapter. GeneReviews an international point-of-care resource for busy clinicians provides clinically relevant and medically actionable information for inherited conditions in a standardized journal-style format covering diagnosis management and genetic counseling for patients and their families.
Each chapter in GeneReviews is written by one or more experts on the specific. The anti-Soviet political behavior of some individuals being outspoken in their opposition to the authorities demonstrating for reform and writing critical books were defined simultaneously as criminal acts eg a violation of Articles 70 or 190-1 symptoms of mental illness eg delusion of reformism and susceptible to a ready-made diagnosis eg. Globalization or globalisation Commonwealth English.
For 50 years and counting ISACA has been helping information systems governance control risk security auditassurance and business and cybersecurity professionals and enterprises succeed. See spelling differences is the process of interaction and integration among people companies and governments worldwide. Opinions on privacy confidentiality medical records PDF AMA Code of Medical Ethics.
All our customer data is encrypted. News tips updates and advice. Breach of Security in Electronic Medical Records.
If you are an entitled government entity pursuant the Georgia Administrative Procedures Act OCGA 50-13-7d contact the State of Georgias Administrative Procedures Division at 678-364-3785 to enable these features for your location. 1302 which act enacted this title and was based on act Dec. Book Reviews Book News and Author Interviews NPRs brings you news about books and authors along with our picks for great reads.
Our services are very confidential. We consider our clients security and privacy very serious. Documents given or required by law or agency rule to be given to the person arrested except as provided in s.
ACM Transactions on Recommender Systems TORS will publish high quality papers that address various aspects of recommender systems research from algorithms to the user experience to questions of the impact and value of such systemsThe journal takes a holistic view on the field and calls for contributions from different subfields of computer science and. Privacy act systems of records notices. Expert guides and analysis for UK and global business.
Our payment system is also very secure. Security refers to measures used to protect information. This bank describes information related to physical administrative and technical security which may include.
Chapter 2 sets out the legal requirements for high-risk AI systems in relation to data and data governance documentation and recording keeping transparency and provision of information to users human oversight robustness accuracy and security. Security complaints and breaches privacy breaches threat and risk assessments workplace violence theft fraud vandalism accidental damages emergency and increased threat situations or threats to the national. 16-ethics and conduct part 374 part 374.
An individual or organization fulfills its confidentiality duties in part by adopting and enforcing appropriate security measures. Every member of FMCA as defined in the Bylaws accepts and agrees that a condition of said membership is the obligation to abide by the FMCA Member Code of Ethics and the other rules and standards of this organization which represent all our endeavors to be good neighbors careful and responsible recreational vehicle owners and operators and good citizens of our. Visit the Code of Medical Ethics page to access additional Opinions the Principles of Medical Ethics and a list of CME courses that are available.
Our community of professionals is committed to lifetime learning career progression and sharing expertise for the benefit of individuals and organizations. Tech Giant Battles Real-Life Rings of Power Trolls Bloom David Bloom published 6 September 22. This chapter was originally added by Pub.
Certain features of this site have been disabled for the general public to prevent digital piracy. The Society for Human Resource Management SHRM is the worlds largest HR association. We will guide you on how to place your essay help proofreading and editing your draft fixing the grammar spelling or formatting of your paper easily and cheaply.
Security in social networking services.

How Will Mobility Automation Change The Society And Urbanscape Of The Future What Can Design Do To Make The Transition To A Driverless World Responsible And

Network Forensics Privacy And Security 1st Edition Anchit Bijalw

An Ethical Approach To Data Privacy Protection
0 Response to "Chapter 5 Digital Security Ethics and Privacy"
Post a Comment